The Control Architecture That Makes Sense in 2025
🧱 Still running your control system like it’s 1995?
Most industrial sites aren’t building from scratch.
They’re fighting to keep obsolete systems alive—and trying to make them secure, cloud-ready, and compliant at the same time.
But here’s the problem:
You can’t modernize by just adding dashboards and firewalls.
You need to rethink how data flows.
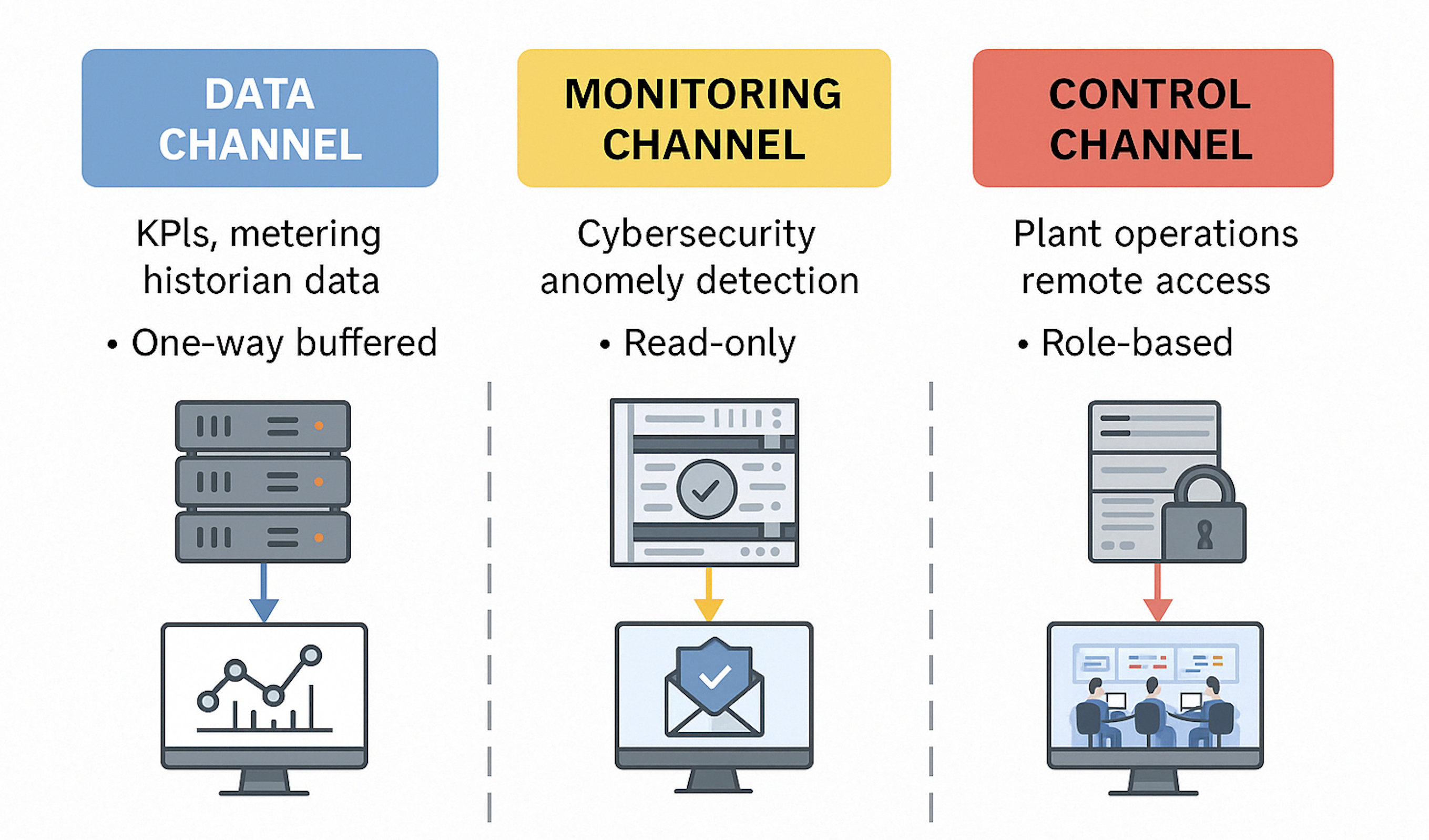
The 3-Channel Architecture That Replaces Purdue
Instead of stacking data in rigid layers, we need to think in channels.
At Bohemia Market, we’ve implemented a new model across power stations, refineries, and solar plants. One that’s already proven.
We call it the Three Channel Model:
🟦 1. The Data Channel
For structured information that flows from OT to IT:
- KPIs, process values, metering data, billing
- Read-only, one-way (often via data diode)
- Buffered and timestamped for accuracy and auditability
This is where billing happens. Where reports are generated. Where predictive maintenance starts.
But let’s be clear:
Prediction doesn’t work when the input is chaos.
“Where there is no information, you cannot fabricate one.”
—Nassim Taleb, Fooled by Randomness
In most ICS environments, data is inconsistent, misnamed, timestamped wrong, or simply misunderstood.
That’s why our Data Channel is structured, governed, and enriched with metadata before it leaves OT.
✅ Use Case:
A power plant billing system now collects accurate data every 6 minutes.
The result? No more disputes. No more penalties. Millions recoveredICS Secure Data Transfe….
🟨 2. The Monitoring Channel
For observability, not control:
- Cybersecurity events, system health, alarms
- Used by SOCs, auditors, compliance teams
- Always non-intrusive, always controlled
✅ Use Case:
Across 11 power stations on three continents, all critical systems are monitored centrally—while keeping full control localICS Secure Data Transfe….
🟥 3. The Control Service Channel
For authenticated, logged, and secured operations:
- Used by service engineers or control room operators
- Access is tightly governed, role-based, and auditable
- Critical during outages, support calls, and remote interventions
✅ Use Case:
In a turbine monitoring deployment, secure VPN tunnels and Active Directory logins allow controlled remote servicing—without exposing the ICS to the internetICS Secure Data Transfe….
Why Channels Beat Layers
Layers blur responsibility.
Channels define it.
- 🔐 Each channel has a purpose, a policy, and a perimeter
- 📦 No channel is open “just in case”
- 🧩 The model scales with your needs—across clouds, sites, and suppliers
This is not theory. It’s already reshaping industrial infrastructure.
Leave a Reply